Scale your AWS security practice without overloading experts
Scale your security practice with access audits optimized for speed & accuracy. Fix issues with complementary automation.
- Create a valuable recurring security audit service at a price clients are happy to pay
- Focus on client-specific analysis & recommendations, not gathering & processing data
- Drastically reduce load on cloud security specialists
- Increase confidence and repeatability of analysis process

Scale IAM security with usable audits & libraries
Scale your security practice with k9 Security’s simple IAM audits and infrastructure code libraries everyone can use.
Cloud security specialists know what the big IAM issues are, but it takes too much work to find them. Let us do the heavy lifting.
Scale risk analysis effort using simple processes that:
- Find and remediate unexpected IAM administrators (also get notified of changes)
- Remove unused IAM users & roles
- Secure access to buckets and keys with supported infrastructure code libraries for Terraform & CDK (GitHub)
Confirm clients actually fixed IAM by verifying expected access in the next report.
Now you have a way to audit and fix clients’ IAM access controls efficiently and scalably.
No overloaded experts.

How to scale your security practice with k9
- k9 reports your clients’ account IAM configurations nightly
- Review IAM access using the k9 Security Katas in Excel, Splunk, or Datadog
- Accelerate delivery of professional audit reports with k9’s report templates and samples
- Get notified of important changes via email or Security Hub
- Help client Cloud teams fix issues by removing excess IAM principal permissions & protecting data with k9’s policy generators
Simple Daily Reporting
k9 analyzes access granted by clients’ AWS security policies nightly, then publishes an actionable report to your own S3 bucket.
Pivot, filter, slice, and dice with tools and data you already use.
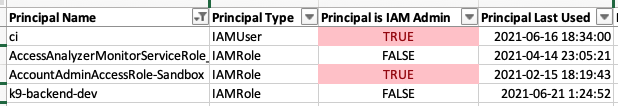
Use the Excel format (sample) for quick, interactive analysis:
Scale access monitoring with pre-built dashboards for Splunk & Datadog:
Who has access to what data? Really. (sample)
k9 tells you exactly what AWS permissions allow today and every day.
k9 determines who has access with the AWS IAM simulation APIs. The analysis covers Service Control, IAM, and Resource policies and integrates external access findings from AWS IAM Access Analyzer.
Use this certified 3rd party IAM access report to audit:
✅ IAM administrators
✅ Unused IAM users and roles
✅ Access to critical data sources, keys, and IAM roles
✅ IAM user passwords and API access keys
✅ Access to AWS service APIs
Supported Services: IAM, STS, KMS, S3, RDS, DynamoDB, Redshift, and more (1375+ AWS API Actions)
Now you can review the critical parts of IAM in minutes, instead of days.
Secure Policy Automation
Secure your clients’ data with security policies generated by k9’s usable infrastructure automation libraries. Built for continuous delivery.
Specify your intended access in simple language and let k9 generate a least privilege security policy.
Use k9 Security’s Terraform & CDK libraries on GitHub for S3 buckets and KMS encryption keys.
✅ Least privilege access policy
✅ Code review
Now your clients can declare least privilege access to data quickly and correctly.
k9 Security is the most usable, scalable, and integrated AWS security policy development and review solution for Cloud teams using continuous delivery. (Just $2.66 per day per account)
Give k9 45 minutes and you’ll learn how to scale your cloud security expertise by more than 3x. Forever.
🎁 When we meet, you’ll learn how to scale IAM engineering and review with k9, we’ll answer your questions about IAM, and give you the Effective IAM for AWS book for your team. 🎁