Fix IAM permissions quickly. Like today.
Cloud teams go fast, safely with simple access audits & automation built for continuous delivery.

Secure IAM with simple audits and libraries
Cloud teams find and fix excess IAM permissions quickly with k9 Security’s usable IAM audits and infrastructure code libraries.
Cloud teams know who should have access to APIs and data, empower them with the how.
Focus and scale risk reduction effort using simple processes that:
- Find and remediate unexpected IAM administrators (also get notified of changes)
- Remove unused IAM users & roles
- Secure access to buckets and keys with supported infrastructure code libraries for Terraform & CDK (GitHub)
Confirm you actually fixed IAM by verifying expected access in the next report.
Now you have a way to audit and fix your IAM access controls efficiently and scalably.
No experts required.
Helping Cloud teams secure IAM at:
The simplest & most scalable way to understand AWS IAM permissions.
+47k
IAM Users & Roles
+10k
Buckets, Keys, & DBs

How to fix IAM with k9
- k9 reports the effective IAM access for principals and resources nightly
- Cloud teams find issues by reviewing IAM access using the k9 Security Katas (or get notified of changes)
- Cloud teams fix issues by removing excess IAM principal permissions & protecting data with k9’s policy generators
Simple Access Reporting
k9 analyzes access granted by your AWS security policies nightly, then publishes an actionable report to your own S3 bucket.
Pivot, filter, slice, and dice with tools and data you already use.
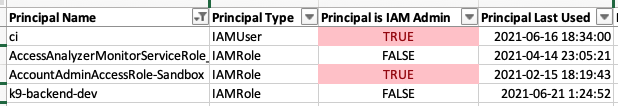
Use the Excel format (sample) for quick, interactive analysis:
Scale access monitoring with pre-built dashboards for Splunk & Datadog:
Who has access to what data? Really. (sample)
k9 tells you exactly what AWS permissions allow today and every day.
k9 determines who has access with the AWS IAM simulation APIs. The analysis covers Service Control, IAM, and Resource policies and integrates external access findings from AWS IAM Access Analyzer.
Use this certified 3rd party IAM access report to audit:
✅ IAM administrators
✅ Unused IAM users and roles
✅ Access to critical data sources, keys, and IAM roles
✅ IAM user passwords and API access keys
✅ Access to AWS service APIs
Supported Services: IAM, STS, KMS, S3, RDS, DynamoDB, Redshift, and more (1375+ AWS API Actions)
Now your whole team can unit test all of your AWS security policies, even in production.
Secure Policy Automation
Secure your data with security policies generated by k9’s usable infrastructure automation libraries. Built for continuous delivery.
Specify your intended access in simple language and let k9 generate a least privilege security policy.
Use k9 Security’s Terraform & CDK libraries on GitHub for S3 buckets and KMS encryption keys.
✅ Least privilege access to data
✅ Code review
Now your whole team can declare least privilege access to data quickly and correctly.
k9 Security is the most usable, scalable, and integrated AWS security policy development and review solution for Cloud teams using continuous delivery.
The quality and depth of expertise demonstrated by K9 security is unparalleled in the industry. K9 has helped advise our AWS IAM strategy and guide a successful implementation of secure identity management that eliminates excess IAM permissions.

Give k9 45 minutes and you’ll learn how to scale your cloud security expertise by more than 3x. Forever.
🎁 When we meet, you’ll learn how to scale IAM engineering and review with k9, we’ll answer your questions about IAM, and give you the Effective IAM for AWS book for your team. 🎁