Scale cloud security within your preferred workflows. More fixes, fewer tickets.
Eliminate the security expert bottleneck and establish cloud access governance with simple access review, policy management, and monitoring processes designed to be used by non-experts in the continuous delivery pipeline. Now cloud and security product teams can easily adopt these capabilities via OEM integration.


Scalable Cloud Access Governance
Helping cloud teams of all sizes scale AWS IAM entitlement management

- Unexpected IAM admins and unused IAM principals.
- Excessive access to critical data and encryption keys.
- Unable to confirm you actually fixed IAM by verifying expected access.
- Security processes slowing continuous delivery.
- Want to achieve least privilege but don’t know how.
- Overloaded experts.
Create an IAM improvement plan with a security expert today!
No excess permissions. No overloaded experts.
The quality and depth of expertise demonstrated by k9 security is unparalleled in the industry. k9 has helped advise our AWS IAM strategy and guide a successful implementation of secure identity management that eliminates excess IAM permissions.
The simplest and most scalable way of managing AWS IAM permissions
Simple Daily Reporting
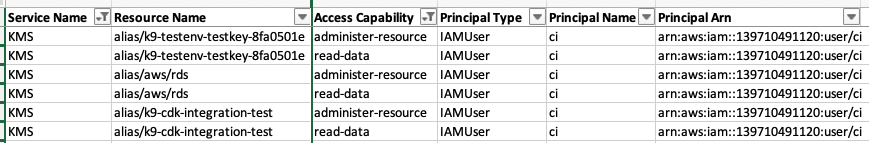
k9 tells you exactly what AWS permissions allow today and every day.
k9 determines who has access with the AWS IAM simulation APIs nightly. The analysis covers Service Control, IAM, and Resource policies plus external access findings from AWS IAM Access Analyzer. Then, actionable reports are published to your own S3 Bucket.
This is not a static analysis of IAM policy or summary of yesterday’s CloudTrail events. (k9 reports what IAM users and roles could do with AWS APIs and data.)
Pivot, filter, slice, and dice with tools and data you already use.
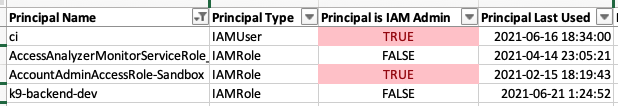
Know exactly who has access to critical data and encryption keys:
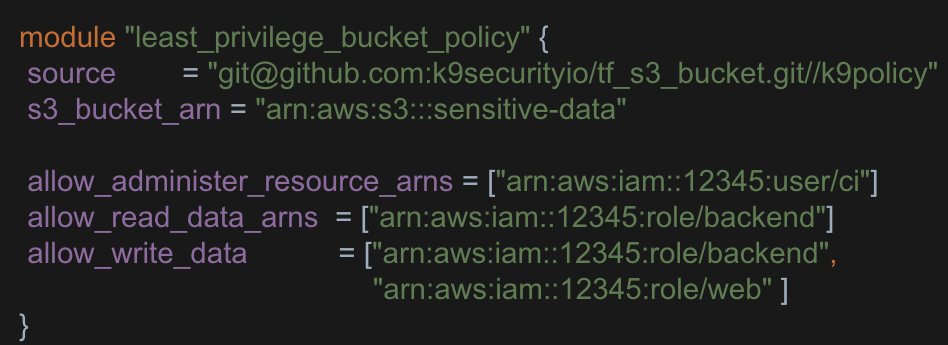
Secure Policy Automation
Cloud teams find issues by reviewing IAM access using the k9 Security Katas.
Specify your intended access in simple language and let k9 generate a least privilege security policy.
See k9 Security’s Terraform & CDK libraries on GitHub for S3 buckets and KMS encryption keys.
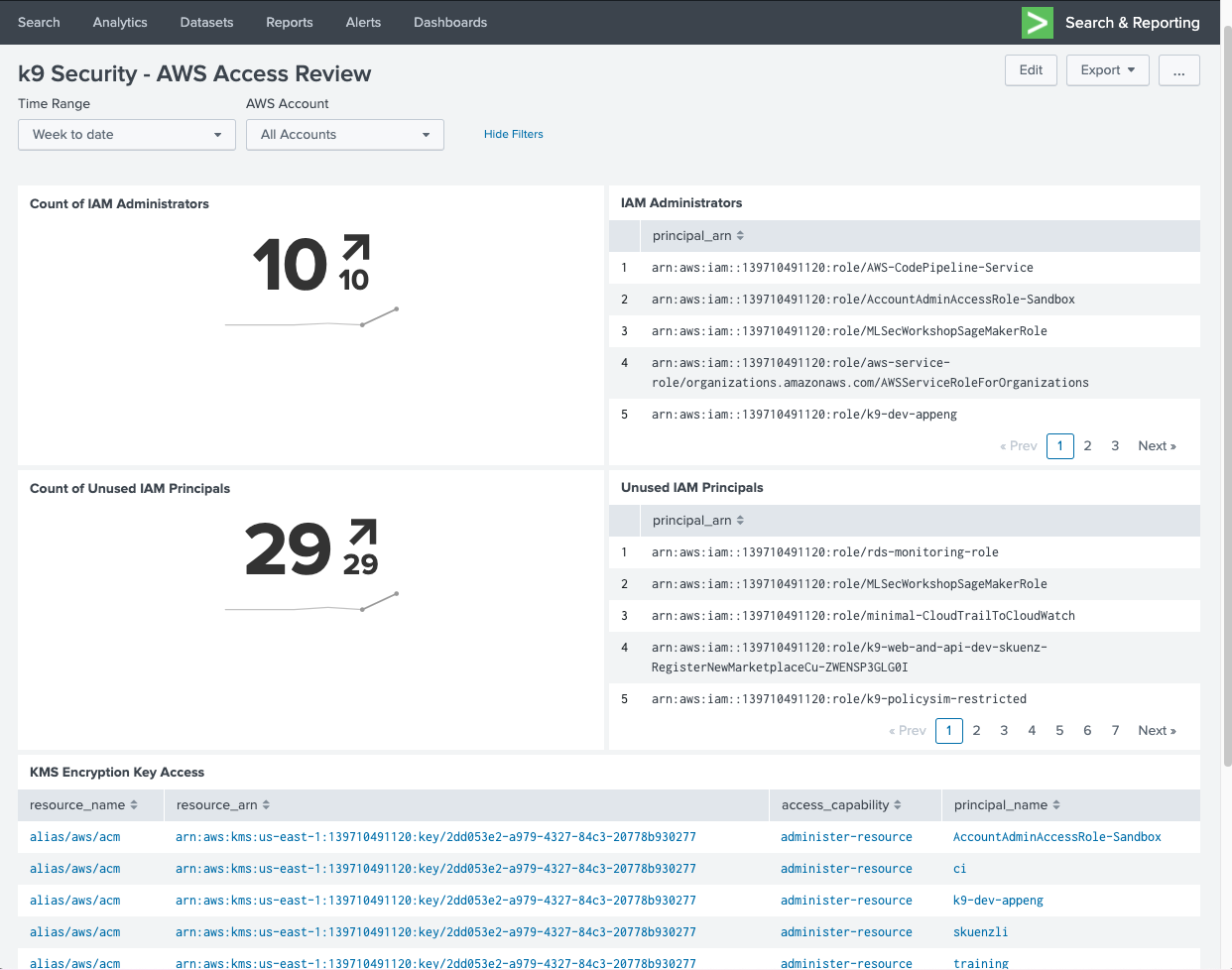
Scale Access Management
Streamline how your organization finds and fixes excess AWS IAM permissions.
Review access with pre-built dashboards for Splunk and DataDog.
Get notified of important access changes via email and AWS Security Hub.
Secure data quickly with simple Terraform and CDK automation that implements best practice in your delivery pipeline.
All built to work with 10s of teams and 100s of resources.
Supported Services: IAM, STS, KMS, S3, RDS, DynamoDB, Redshift, and more…
(2,000+ AWS IAM permissions)
IAM doesn’t have to be hard.
Scale up without security slowing you down
Cloud teams reduce the risk of accidents and data breaches with k9’s usable security automation and IAM access reporting.
Now you can finally secure IAM at the speed of continuous delivery.
Monitoring…
IAM users & roles
Buckets, Keys, & DBs
Simple
95% less time spent on IAM
Secure
Quickly improve your security with usable infrastructure code and expert support. We provide you with step by step processes that eliminate policy guesswork.
Production-ready Terraform & CDK
Scalable
5 optimized audit processes
