Scale your Security Practice
k9 Security helps you scale your AWS security practice by providing a consistent, repeatable way to assess and improve the security of your customers’ AWS accounts. k9 simplifies analysis of access controls, assessment and prioritization of risk to resources and data, and guides security policy improvements with robust infrastructure code libraries.
The Nature of The Problem
Modern delivery practices and self-service help customers deliver changes quickly and at high throughput. However, those changes may introduce vulnerabilities that even security experts find challenging to understand and improve. Worse, it takes an incredible amount of time to find those vulnerabilities and remediate them. Here are just a few of the challenges you are likely facing:
The Rate Of Security Changes Outpaces Security Expertise
It’s difficult at best to keep up with the volume of changes happening at clients, especially for new applications that use new Cloud services.
Manual inspection Does. Not. Scale.
You cannot hire or train security experts quickly enough.
Cloud IAM Systems Are Complex In Many Ways
Cloud IAM systems are very complex, and even your Cloud Security Engineer has trouble working out what access capabilities a given policy allows in your universe and interactions with other applications and new capabilities launched by AWS.
Summarizing Access Control Problems Is Hard
It’s difficult to summarize access control problems for your own direct analysis let alone in a way that you can easily share with your own team or other teams.
Modeling thousands of AWS API actions and their effects from scratch wastes your time.
Free your security experts from manual analysis of AWS IAM and resource policies and help them elevate discussion of access controls to a language everyone on the team can understand — even customers.
k9 automatically, accurately, and tirelessly analyzes the effective access each IAM user or role has to critical data services and individual resources, such as an S3 bucket. Access reports describe access capabilities using simple, understandable language you can adopt within your team.
k9 was built to help your security team and your platform’s customers collaborate, ship safely and sleep well.
Practice Safe DevSecOps
k9 is like having an AWS Security expert integrated into your delivery workflow, giving you the visibility you need, and advising you about the security and risk of your security policies: IAM, SCP, resource.
Prevent Customer Data Breaches and Scale By:
-
Answering ‘simple’ questions with very complex answers like “who has access to what data, compute resources, and APIs?” and helping you understand the risk of that access using the k9 access capability model
-
Providing consistent, reliable information security and operational teams need to scale security review and improvement processes, especially with those who are not experts in AWS.
-
Helping you say “yes, here’s how” to application teams while effectively managing access control risk with a minimum of effort – during normal business hours.
-
Finding access control problems in an AWS account quickly and offering quick-to-implement solutions.
Simplify the Complex AWS Access Control Model
k9 reports what access each application and person has to each Cloud resource in language everyone can understand.
This accurate, automated analysis eliminates the need for mind-bending IAM thought experiments and tedious, time consuming manual report generation.
Examples
- the ci user has administer-resource, delete-data, read-data for all resources (should it? what about the prod DB?)
- the security-audit role has read-data for all resources
- the ecommerce-web role has write-data and read-data for only the orders bucket
Simple Daily Reporting
k9 analyzes access granted by your AWS security policies nightly, then publishes an actionable report to your own S3 bucket.
Pivot, filter, slice, and dice with tools and data you already use.
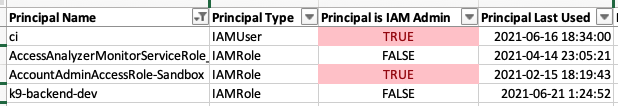
Use the Excel format (sample) for quick, interactive analysis:
Scale access monitoring with pre-built dashboards for Splunk & Datadog.
Use the certified 3rd party IAM access report to audit:
✅ IAM administrators
✅ Unused IAM users and roles
✅ Access to critical data sources, keys, and IAM roles
✅ IAM user passwords and API access keys
✅ Access to AWS service APIs
Supported Services: IAM, STS, KMS, S3, RDS, DynamoDB, Redshift, and more (1375+ AWS API Actions)
Secure Policy Automation
Secure your data with security policies generated by k9's usable infrastructure automation libraries. Built for continuous delivery. Specify your intended access in simple language and let k9 generate a least privilege security policy. See k9 Security's Terraform & CDK libraries on GitHub for S3 buckets and KMS encryption keys.
✅ Least privilege access policy
✅ Code review
Who has access to what data? Really. (sample)
k9 tells you exactly what AWS permissions allow today and every day.
k9 determines who has access with the AWS IAM simulation APIs. k9 summarizes that into actionable reports (details). Analysis includes Service Control, IAM, and Resource policies.
This is not a static analysis of IAM policy or summary of yesterday's CloudTrail events. (k9 reports what IAM users and roles could do with AWS APIs and data.)
Now you can "unit test" all of your AWS security policies, even in production.
How k9 Works
The k9 access inventory generation process pulls data from the AWS IAM and data services for your account and summarizes it once you’ve provided k9 access(sample report in xlsx). The inventory process enumerates IAM entities and assess access to resource types supported by k9. The assessment process uses the IAM policy simulation API to ask AWS who has access to what, which is really the only way to be sure about such things. This description glosses over a lot of detail, particularly that this assessment process requires deep knowledge of the AWS security model, careful data modeling, and usually requires a large number of queries to the IAM service, even when highly optimized (don’t worry: AWS IAM API usage is free).
The inventory generation process runs at least once per 24 hour period in which there are changes to IAM or resources. The inventory process generates a report encrypted with the customer’s KMS encryption key and stored in an internal k9-managed S3 bucket. Then k9 publishes this report to a customer-managed Secure Inbox implemented using an S3 bucket and KMS.
k9 summarizes each IAM user or role’s provisioned access to AWS resources into a small number of access capabilities:
- administer-resource
- read-config
- use-resource
- read-data
- write-data
- delete-data
- unclassified-access
Certain actions may classify to multiple capabilities. For example, the rds:DeleteDBCluster action classifies to both delete-data and administer-resource because deleting the DB cluster deletes both the DB instances and the cluster’s data volume. Quick question: who can delete your production data?
Interested in learning more about how k9 works? Check out our How k9 Works page.
Configuring k9 Is Easy
Configuring k9 access is a very simple and painless process.
SignUp
The signup process is quick whether for a limited trial or full account.
configure
Configure k9 access to your AWS accounts quickly using our secure, simple, and reviewable process.
Analyze Access
Use k9’s access inventory report delivered to your S3 Secure Inbox each day to identify excess privileges and risks in your environment.
"Understanding and managing our complicated AWS IAM ecosystem has never been this simple or painless."
– Kenneth K. Slachta, Jr. – VenturPlex, LLC