Secure AWS data with usable policy automation and audit
Go Fast, Safely
Usable AWS Security & Audit for the entire team
Protect data in AWS, quickly and confidently. Cloud teams improve security policies and accelerate continuous delivery with k9’s usable automation and audit tools. Wield the full power of AWS security easily with k9 Security, available in AWS Marketplace.
Understand who exactly has access to your data in AWS, finally. Discover your risks. Audit and track your compliance continuously with comprehensive & accurate daily reporting.
Secure your data by defining and deploying better security policies through your infrastructure code pipelines using CDK or Terraform today.
Simplify the AWS security model with k9 so you can improve AWS security with every deploy and audit access continuously.
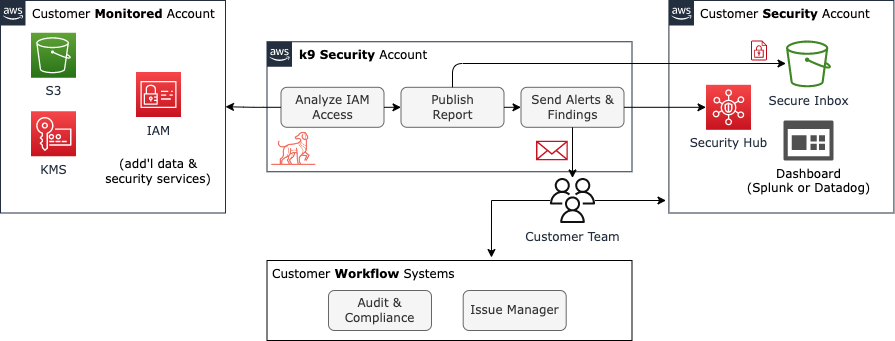
Solution Architecture
k9 analyzes your AWS accounts and determines what access each IAM user and role has to core AWS data and security services, and to the specific S3 data and KMS encryption key resources in your account. k9’s analysis is built on tens of thousands of (free) simulations using the AWS IAM simulation APIs, so you can trust it’s correct and accounts for all of your actual AWS security policies: SCP, Resource, and IAM.
Then k9 compiles that analysis and reports access capabilities in terms everyone can understand: administer-resource, read-config, use-resource, read-data, write-data, delete-data.
k9 encrypts and delivers these access inventory reports to your own secure inbox nightly. Access inventory reports are ready for review by security analysts, auditors, platform engineers, and delivery teams responsible for security of application data. Reports delivered in JSON, CSV, and Excel formats (sample – xslx).
Monitoring…
IAM users & roles
Buckets, Keys, & DBs
Actually Understand & Improve Access Controls
Understand
Answer questions like:
- Who can administer IAM? Which IAM users and roles are unused?
- Who can access sensitive data in S3? Decrypt encrypted data?
- Who can delete the production database? (what about your
continuous-integrationuser? Find out!)
Continuously audit your AWS environment and verify compliance with access controls required by SOC 2, ISO27001, PCI, and HIPAA.
k9 Security delivers access reports ready to review and act-upon in JSON, CSV, and Excel formats (sample – xslx).
Thank you for your guidance and analysis of our legacy production environments. Visibility from k9 in concert with the centralization of the data is key for us here.
Secure
Fix security policy problems with k9’s complementary policy generation libraries for AWS CDK & Terraform. Specify who should have access using the simplified k9 access capability model. k9 infrastructure code libraries generate a best practice policy right within your delivery pipeline.
Now you can finally scale continuous security policy review and improvement out to your application teams.
The k9 S3 and KMS resource policies are so much better than what we have now and what CDK generates with “add read and write permissions.”
Get Started with k9 Security Today
Ready to get started? k9 security will deliver access assessments to your secure inbox with simple pay-as-you-go and pay-for-what-you-use pricing once you subscribe in AWS Marketplace and deploy k9 monitoring components using CloudFormation. Let k9 Security help you get the most out of AWS Security services Go Fast, Safely.