Configure k9 Access to AWS Accounts
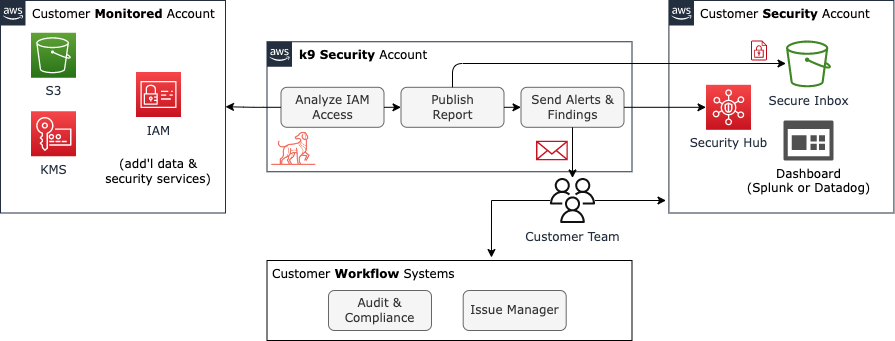
This document describes how to configure k9’s access to your AWS accounts so that it can audit the accounts and deliver the reports to you. Here is a logical view of what we are creating:
In this process, we will create:
- Secure Inbox Bucket and Encryption Key in your security account
- Auditor Role(s) in your monitored AWS accounts
It’s ok if you have a single AWS account. Create both the audit and secure inbox resources in that account.
These resources will be created automatically by the CloudFormation templates referenced in the steps that follow.
Step-by-step guide
General Notes
Please use the us-east-1 AWS region for these steps. Security policies for using KMS encryption have region-specific details and the automation is only supported for us-east-1 currently.
These resource creation steps use an Environment parameter. This parameter identifies the k9 environment you will be using and ultimately the AWS account ID that your AWS accounts will trust to monitor and deliver reports. Use the production k9 environment (prod) unless debugging an issue with the k9 Operations team.
Step 0 – Gather Information
Please gather this information before starting the resource provisioning process.
KeyAdministratorARN – The ARN of IAM user or role in the Security account that will administer the encryption key used to protect the k9 reports. This can be any user or role that you trust with this sensitive data.
K9CustomerID – The k9 Customer Id generated for your organization during registration or provided to you, e.g. C123456. Contact k9 Support if you are unsure of your Customer Id.
Step 1 – Create Resources for Report Delivery
The first step is to create an S3 bucket and KMS encryption key in the security account where your reports will be delivered to.
While logged into your Security or ‘Secure Inbox’ AWS account, you can grant k9 access by clicking on this link:
The report delivery configuration has a few required parameters and some optional parameters:
K9CustomerID and KeyAdministratorARN, as above.
SecureInboxBucketName – The name of a new S3 bucket which k9 will deliver reports to, e.g. mycompanyname-secure-inbox.
LatestReportsEnabled – (Optional) Deliver a copy of the latest reports to each monitored account’s ‘latest’ directory to simplify finding the latest reports. Useful for Datadog integrations.
SendAlertsToSecurityHub – (Optional) Send IAM access change alerts to AWS Security Hub
HiveReportsEnabled – (Optional) Deliver a copy of the reports for use with Athena with S3 object keys named with Hive-style partitioning. Useful for the AWS Athena and Config integrations.
NotifyReportCreationEvents – (Optional) Send S3 object creation events for latest CSV reports to SNS and an SQS queue. Useful for Splunk and custom integrations.
AlertsEmailAddress – (Optional) Send IAM access change alerts to the configured email address.
All are documented within the template.
The report resource configurations will be reported to k9 automatically during the provisioning process. You can inspect the resources that were created in the stack’s Outputs tab.

Alternatively, you can download the template from S3 (source), review it, and and deploy using the aws cli directly:
# Configure the '<REPLACE_ME>' values appropriately/usr/local/bin/aws cloudformation deploy \ --stack-name k9-report-publisher \ --template-file $(pwd)/configure-k9-resources-for-report-delivery.template \ --capabilities CAPABILITY_NAMED_IAM \ --parameter-overrides \ K9CustomerID=<REPLACE_ME> \ SecureInboxBucketName=<REPLACE_ME> \ KeyAdministratorARN=<REPLACE_ME>The second step is to create a k9-auditor role for each AWS account you would like k9 to monitor. This auditor role uses the AWS-defined SecurityAudit managed policy purpose built for security audits (arn:aws:iam::aws:policy/SecurityAudit).
The optional EnableOrgAudit parameter determines whether k9 should try to gather and audit organization-wide services such as AWS Identity Center and Service Control Policies. Only enable this from the Management account or a Delegated Administrator account. Organization level information cannot be gathered from standard ‘member’ AWS accounts.
This step generates a unique External ID that k9 will use to assume the auditor role created in your monitored AWS account(s). The External ID improves the security of the trust relationship between k9 and the monitored account (details).
While logged into your AWS account, you can grant k9 access by clicking on this link:
- To enable analysis of Service Control policies and/or AWS Identity Center integration, you should set the
EnableOrgAuditto parameter to ‘yes‘ in an account that is a delegated admin (preferred) or the management account. If you have deployed AWS Identity Center, Config, GuardDuty or another security service to a dedicated account, then that account is a delegated admin and the organization audit feature can be enabled there. - You can use CloudFormation StackSets to deploy the auditor stack to your entire AWS Organization or particular Organizational Units.
The k9 Support team is happy to assist or answer questions.
The auditor role configurations will be reported to k9 automatically during the provisioning process. You can inspect the resources that were created in the stack’s Outputs tab.

Alternatively, you can download the template from S3 (source), review it, and and deploy using the aws cli directly:
# Configure the '<replace me>' values appropriately/usr/local/bin/aws cloudformation deploy \--stack-name k9-account-auditor \ --template-file $(pwd)/configure-k9-resources-for-monitored-account.template \ --capabilities CAPABILITY_NAMED_IAM \ --parameter-overrides K9CustomerID=<REPLACE_ME> Step 3 – Enable Security Hub Findings (Optional)
You can enable k9 Security to send IAM access findings to Security Hub to help you operationalize AWS IAM management. To do that:
- Ensure you enabled the Security Hub integration when deploying the Report Delivery account automation in Step 1
- Subscribe to k9 Security findings by navigating to the k9 Security option in the Security Hub Integrations in the AWS console and clicking ‘Accept Findings’
Step 4 – Confirm configuration
The k9 Support team will email the technical contact provided during customer registration with confirmation that your report delivery and account monitoring has been configured correctly or corrective actions. Reporting will begin after delivery details are confirmed.
Resources
k9 Security operates from these AWS accounts, which you will see referenced within the CloudFormation templates:
- k9-dev:
139710491120 - k9-prod:
826438284864